Cisco Open-Sources Foundation-sec-8B: A Cybersecurity-Focused AI Model Built for Modern Threats

In today’s increasingly digitized world, cybersecurity threats have evolved in complexity and frequency, posing unprecedented risks to individuals, organizations, and national infrastructures alike. The rise of sophisticated attack vectors, such as ransomware, polymorphic malware, and AI-driven exploits, underscores the growing necessity for advanced defense mechanisms. Traditional rule-based security systems, though foundational, are rapidly proving inadequate in identifying and neutralizing these emergent threats in real-time. In this dynamic landscape, the integration of artificial intelligence (AI) into cybersecurity practices is not just beneficial—it is imperative.
Artificial intelligence has emerged as a transformative force in the field of cybersecurity, offering capabilities far beyond what conventional tools can provide. From anomaly detection and behavioral analysis to automated threat hunting and predictive intelligence, AI technologies are being leveraged to enhance both the efficiency and effectiveness of security operations. Among these advancements, the development of domain-specific AI models has gained significant traction. These models are trained on cybersecurity-centric datasets, enabling them to deliver context-aware insights that improve detection accuracy and reduce false positives. Consequently, the cybersecurity industry is witnessing a paradigm shift wherein AI is becoming a central pillar of defense strategies.
Amidst this evolution, Cisco has positioned itself at the forefront of AI-driven cybersecurity innovation. Recognizing the limitations of generic language models in handling complex security scenarios, the company has introduced a groundbreaking solution: the Foundation-sec-8B model. This open-source AI model is designed explicitly for cybersecurity applications, trained on a highly specialized corpus of threat intelligence data. It represents a pivotal advancement in the domain, addressing both technical and strategic challenges that security teams face today.
The launch of Foundation-sec-8B signals a broader trend in which leading technology firms are not only adopting AI for internal use but are also contributing to the open-source ecosystem. Cisco’s move aligns with a growing recognition that collaborative innovation is essential to counteract the rapidly expanding threat landscape. By open-sourcing a highly capable model, Cisco empowers the broader cybersecurity community—including smaller firms and independent researchers—to build, test, and deploy advanced threat detection systems without prohibitive costs.
This blog post delves into the implications of Cisco’s strategic initiative. It will explore the technical foundations and capabilities of the Foundation-sec-8B model, assess its performance against industry benchmarks, and consider its potential to reshape cybersecurity operations across sectors. Through comparative analysis and visual data representation, we will highlight how this AI model distinguishes itself from its peers and why it matters. More importantly, we will examine the broader significance of open-source AI in democratizing access to robust cybersecurity tools.
In the sections that follow, we will offer a detailed look at the Foundation-sec-8B model—its architecture, training methodology, and intended use cases—alongside empirical evaluations of its performance. We will also consider the model’s role in fostering collaboration and innovation within the security community. As organizations navigate a world fraught with digital peril, Cisco’s open-source AI model stands as a compelling example of how cutting-edge technology, when made accessible, can serve as a bulwark against cyber threats.
Unveiling Foundation-sec-8B: Cisco's Open-Source Cybersecurity AI Model
The proliferation of increasingly sophisticated cyber threats has compelled organizations to rethink their approach to digital defense. Recognizing that traditional threat detection mechanisms are struggling to keep pace, Cisco has responded with a novel solution that merges deep learning with domain-specific intelligence: the Foundation-sec-8B model. This open-source large language model (LLM) represents a substantial leap forward in the application of artificial intelligence to cybersecurity. It is not merely a general-purpose AI model retooled for security tasks, but a model explicitly architected and trained with a cybersecurity-first perspective. The release of Foundation-sec-8B by Cisco marks a pivotal moment in the intersection of open-source development and enterprise-grade cybersecurity innovation.
Strategic Foundations and the Genesis of the Model
The development of Foundation-sec-8B is rooted in Cisco’s broader strategic vision to transform the cybersecurity landscape through AI-driven innovation. This initiative gained momentum with the acquisition of Robust Intelligence in early 2024, a company known for its expertise in adversarial robustness and AI safety. Post-acquisition, Cisco consolidated internal talent and domain experts under its newly formed Foundation AI team, tasked with developing highly specialized AI models for enterprise-grade use cases. Foundation-sec-8B is the first major outcome of this effort.
This model is distinguished by its deliberate departure from generic large language models, which often lack the granularity needed for effective cybersecurity interventions. Instead, Foundation-sec-8B is the product of a focused endeavor to build a model that is purpose-trained on cybersecurity-relevant datasets and optimized for the specific linguistic and contextual patterns found in threat intelligence data.
Technical Design and Model Architecture
Foundation-sec-8B is built atop Meta’s Llama 3.1 architecture, a well-established open-source LLM framework that balances scalability with efficiency. The model boasts 8 billion parameters—placing it firmly in the mid-sized model category—allowing for a judicious tradeoff between performance and hardware requirements. Importantly, the model was trained using approximately 5 billion tokens of curated cybersecurity-specific text. This includes vulnerability reports, incident response documentation, red team and blue team playbooks, MITRE ATT&CK tactics and techniques, and open-source threat intelligence feeds.
The model training pipeline incorporated industry-leading best practices to ensure accuracy, contextual understanding, and reduced hallucination. Cisco leveraged Reinforcement Learning from Human Feedback (RLHF) techniques to fine-tune the model for real-world decision-making scenarios common to Security Operations Centers (SOCs) and DevSecOps workflows. Special emphasis was placed on few-shot and zero-shot capabilities, enabling the model to perform effectively even when confronted with novel or ambiguous threat contexts.
Open-Source Licensing and Community Engagement
A key aspect of Cisco’s initiative is its commitment to open-source principles. Foundation-sec-8B has been released under the Apache 2.0 license—a permissive open-source license that allows both academic and commercial use without restrictive conditions. The model, along with its tokenizer and relevant documentation, is publicly accessible on the Hugging Face platform, facilitating widespread adoption and community-driven enhancements.
By releasing this model as open source, Cisco is not merely providing a tool—it is inviting collaboration. Security professionals, researchers, and developers are encouraged to contribute use-case adaptations, share evaluation results, and propose enhancements. This communal development model is especially vital in cybersecurity, where collective intelligence often outpaces isolated efforts.
Purpose-Built Capabilities and Use Cases
What sets Foundation-sec-8B apart is its alignment with cybersecurity tasks from the ground up. Rather than relying on generic knowledge representations, this model is imbued with a deep contextual understanding of the cybersecurity lexicon. For example, it can differentiate between high-severity vulnerabilities (e.g., CVSS 9.8 remote code execution exploits) and benign anomalies, evaluate system logs in the context of known indicators of compromise (IOCs), and generate detailed incident summaries suitable for executive-level reporting.
Foundation-sec-8B is already being piloted in diverse operational environments, including:
- Threat Detection and Response: Identifying and prioritizing real threats from SIEM alerts using enriched context.
- Vulnerability Analysis: Parsing vulnerability databases and generating remediation recommendations.
- Red Team Simulation: Crafting adversarial playbooks and simulating realistic attack scenarios.
- DevSecOps Automation: Reviewing codebases and CI/CD pipelines for security weaknesses using natural language instructions.
In essence, Foundation-sec-8B acts as an intelligent assistant for cybersecurity professionals, augmenting human expertise with machine-scale precision and recall. It is designed to reduce alert fatigue, improve detection accuracy, and accelerate decision-making within critical threat windows.
The following chart illustrates how Foundation-sec-8B compares to general-purpose AI models in terms of training specificity, parameter efficiency, hardware requirements, and use-case alignment:
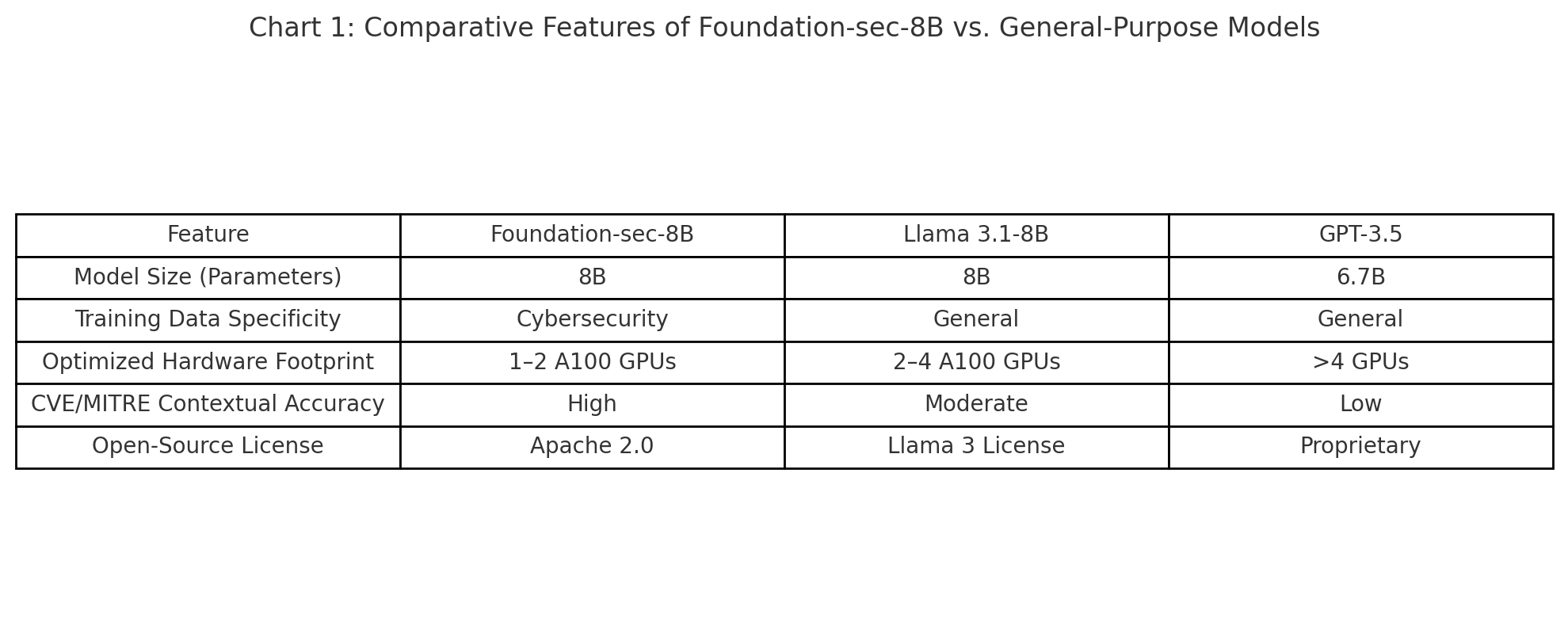
As the chart demonstrates, Foundation-sec-8B strikes a unique balance between model specificity and operational efficiency, positioning it as a highly practical tool for cybersecurity teams of all sizes.
Benchmarking and Performance Analysis
The efficacy of any artificial intelligence model, particularly one designed for critical applications such as cybersecurity, is ultimately determined by its performance against well-established benchmarks. Cisco’s Foundation-sec-8B has been rigorously evaluated using a suite of domain-specific assessment tools to measure its accuracy, relevance, and adaptability in real-world cybersecurity contexts. This section provides a detailed analysis of how Foundation-sec-8B compares with other leading models, highlights its performance metrics, and explores its practical applicability within security operations environments.
Evaluation Framework and Methodology
Cisco employed a comprehensive benchmarking framework to evaluate Foundation-sec-8B, ensuring that the model’s capabilities were tested across a diverse range of cybersecurity tasks. Two key benchmarks—CTI-MCQA (Cyber Threat Intelligence Multiple-Choice Question Answering) and CTI-RCM (Reasoning with Cybersecurity Materials)—were utilized to measure the model’s domain understanding and reasoning capabilities. These benchmarks are designed to test not only knowledge recall but also the ability to interpret complex threat intelligence scenarios, analyze security events, and propose actionable insights.
The evaluation datasets included real-world vulnerability reports, security advisories, threat actor profiles, and simulated incident response narratives. Each benchmark task required the model to generate or select responses with a high degree of contextual relevance. Cisco compared the performance of Foundation-sec-8B with that of Meta’s Llama 3.1-8B and Llama 3.1-70B models, both of which represent current state-of-the-art open-source LLMs. The results were measured using standardized accuracy scores and contextual precision metrics, reflecting the model’s understanding of security-specific terminology, threat modeling frameworks, and adversarial behavior patterns.
Benchmarking Results and Key Findings
The benchmarking results affirm that Foundation-sec-8B performs exceptionally well relative to its peers, especially given its modest parameter count. The model scored 67.39 on CTI-MCQA and 75.26 on CTI-RCM—figures that not only surpass the Llama 3.1-8B’s performance but also come remarkably close to those of the much larger Llama 3.1-70B. These results underscore the effectiveness of Foundation-sec-8B’s cybersecurity-specific training corpus and architectural optimization.
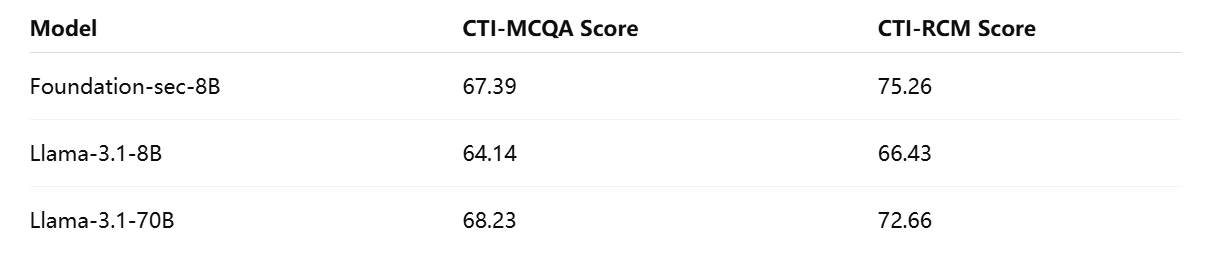
As the table illustrates, Foundation-sec-8B is not only competitive but in certain scenarios superior to much larger models. This is particularly noteworthy considering the cost and infrastructure implications associated with training and deploying 70B parameter models. The relatively narrow performance gap between Foundation-sec-8B and Llama 3.1-70B suggests that domain-specific training can yield efficiency gains that rival brute computational scale.
Performance Efficiency and Hardware Requirements
One of the most critical advantages of Foundation-sec-8B lies in its operational efficiency. Unlike monolithic LLMs that require large-scale GPU clusters for inference and fine-tuning, Foundation-sec-8B can operate effectively on as few as one or two NVIDIA A100 GPUs. This accessibility makes the model a feasible option for mid-sized security operations teams and resource-constrained organizations that may not have access to high-performance computing environments.
Furthermore, the model supports quantized inference, allowing deployment on edge devices and within containerized environments. This makes it particularly well-suited for integration into Security Information and Event Management (SIEM) platforms, threat-hunting tools, and DevSecOps pipelines. Cisco has also reported that inference latency is significantly reduced compared to similar-scale models, enabling faster threat response and real-time decision-making.
Use Cases and Real-World Applications
Beyond raw benchmarking scores, the true measure of an AI model's value lies in its capacity to generate impact in real-world scenarios. Foundation-sec-8B excels in a wide range of use cases where deep contextual awareness and domain specificity are essential:
- Security Operations Centers (SOCs): Analysts can use the model to triage alerts, summarize incident timelines, and generate forensic insights more efficiently than manual methods or general-purpose LLMs.
- Vulnerability Management: By parsing CVEs and correlating them with exploit databases and affected asset inventories, the model aids in prioritizing remediation based on risk.
- Threat Intelligence: The model can synthesize threat actor profiles and derive Indicators of Compromise (IOCs) from fragmented intelligence sources, enhancing situational awareness.
- Automated Documentation: It can draft post-incident reports and security policy updates that align with compliance frameworks such as NIST, ISO 27001, and CIS Controls.
In each of these domains, Foundation-sec-8B not only accelerates routine processes but also enriches them with AI-driven insights that were previously unattainable using conventional tools. The ability to fine-tune or instruct the model on organization-specific security policies further expands its applicability.
Interpretability and Trustworthiness
Another factor contributing to the model’s performance is its design for transparency and interpretability. Unlike black-box solutions, Foundation-sec-8B includes integrated mechanisms for explanation generation, allowing users to trace how conclusions were reached—an essential capability in regulated industries and forensic investigations. Cisco also incorporated adversarial robustness testing during training to minimize risks of prompt injection, misinformation propagation, or manipulation by malicious actors.
Moreover, through continual feedback mechanisms and community contributions on platforms like Hugging Face, the model’s decision-making heuristics are expected to improve over time. Cisco has committed to releasing regular updates and model variants tailored to different cybersecurity domains, including cloud security, OT/ICS security, and zero-trust architectures.
Integration and Deployment: Bringing Foundation-sec-8B into Real-World Security Environments
The effectiveness of an AI model in cybersecurity is not solely determined by its architectural design or benchmark performance—it is also defined by its ease of integration and ability to deliver actionable insights in live security environments. Foundation-sec-8B, with its flexible design and open-source architecture, has been engineered for rapid and scalable deployment across a wide array of cybersecurity infrastructures. This section explores how organizations can embed Foundation-sec-8B into their operational workflows, the various deployment strategies available, and the real-world architectural considerations that enable its optimal use.
Deployment Options and Infrastructure Compatibility
One of the most compelling features of Foundation-sec-8B is its deployability on commercially available hardware. While many state-of-the-art models demand extensive GPU resources, Foundation-sec-8B can be fine-tuned and inferred using only one or two NVIDIA A100 GPUs, making it feasible for mid-sized enterprises and academic institutions. Cisco also provides quantized versions of the model to facilitate deployment on resource-constrained environments, including containerized and edge-compute platforms.
For organizations leveraging cloud infrastructure, Foundation-sec-8B can be deployed via Kubernetes clusters, Docker containers, or serverless architectures using model hosting platforms such as Hugging Face Inference Endpoints, AWS SageMaker, or Azure Machine Learning. Cisco offers pre-built integration modules and SDKs to support common deployment pipelines, further accelerating adoption and minimizing configuration overhead.
In on-premise environments, the model can be incorporated into existing SOC infrastructures by running on air-gapped servers or integrated into virtual security appliances. These options are particularly relevant for government agencies and regulated industries where data locality and sovereignty are paramount.
Integration with Security Platforms and Tools
To ensure broad applicability, Foundation-sec-8B is designed to interoperate with the most widely used cybersecurity platforms and tools. Security Information and Event Management (SIEM) systems such as Splunk, IBM QRadar, and Microsoft Sentinel can consume insights generated by Foundation-sec-8B through APIs or custom connectors. The model can analyze incoming alerts, correlate threat patterns, and provide natural language summaries and prioritization cues that improve analyst throughput.
In Security Orchestration, Automation, and Response (SOAR) platforms, the model can assist in automating playbook generation, incident triage, and alert enrichment. For example, a suspicious login detected by a SIEM system can be automatically fed to Foundation-sec-8B for contextual analysis, which then informs the SOAR platform whether to escalate the incident, isolate the endpoint, or await additional indicators.
Moreover, the model’s compatibility with CI/CD pipelines enables its use in DevSecOps environments. Developers and security engineers can leverage Foundation-sec-8B to analyze Infrastructure as Code (IaC) scripts, identify misconfigurations, and recommend secure coding practices directly within development environments. This reduces the lag between code writing and security validation, embedding AI-driven vigilance into the software development lifecycle.
Customization and Fine-Tuning for Specific Use Cases
While the base model is robust and generalizable across many cybersecurity domains, Foundation-sec-8B supports further fine-tuning to suit organization-specific needs. Cisco provides guidance and scripts for continued pretraining or domain-specific fine-tuning using additional datasets, such as internal incident reports, proprietary telemetry, or vertical-specific compliance standards.
Enterprises can, for instance, fine-tune the model to better detect threats unique to their sector—such as ATM malware in the banking industry or SCADA exploits in energy infrastructure. Similarly, multilingual capabilities can be enhanced by augmenting the model with security datasets in non-English languages, thereby expanding its usability across global security teams.
Moreover, Cisco’s roadmap includes a plug-in ecosystem for Foundation-sec-8B, enabling developers to build domain-specific extensions for use cases such as phishing detection, insider threat monitoring, and legal compliance automation.
Operational Considerations and Best Practices
Successful deployment of Foundation-sec-8B requires more than technical readiness—it also involves the implementation of responsible AI governance. Cisco recommends incorporating human-in-the-loop review systems, especially in high-stakes decisions, to ensure that model outputs are interpreted and acted upon with human oversight.
Logging and observability are also crucial. Organizations are advised to maintain detailed logs of model queries, outputs, and decision pathways for auditing, compliance, and retraining purposes. Integration with observability stacks such as Prometheus, Grafana, or OpenTelemetry can help monitor model behavior in production.
Lastly, cybersecurity teams should implement red-teaming exercises and adversarial testing to assess the model’s resilience to prompt injection, bias, and false positives. These practices ensure that Foundation-sec-8B operates as a trustworthy and secure AI agent within organizational workflows.
Enabling a New Paradigm of AI-Augmented Security
The integration of Foundation-sec-8B into security environments signifies a transition from reactive, manual processes to proactive, intelligence-driven security operations. The model's real-time inference capabilities, low-latency architecture, and interoperability make it an ideal candidate for next-generation SOCs—where automation, scale, and contextual awareness are key performance drivers.
As organizations continue to confront increasingly complex threat landscapes, Foundation-sec-8B offers a practical and transformative approach to AI-enhanced cybersecurity. Its thoughtful design for integration and deployment ensures that it is not just an academic exercise or proof of concept, but a deployable, high-impact tool that can materially improve threat detection, incident response, and operational resilience.
Implications for the Cybersecurity Community
The release of Cisco’s Foundation-sec-8B open-source AI model has far-reaching implications for the global cybersecurity community. At a time when adversarial threats are growing in both volume and sophistication, the availability of a high-performance, domain-specific AI model represents a significant step toward democratizing access to advanced cybersecurity capabilities. Beyond its technical attributes, Foundation-sec-8B embodies a strategic pivot in how cybersecurity tools are developed, shared, and operationalized. This section explores how the model is poised to reshape industry practices, foster collaboration, and set a precedent for future AI development in cybersecurity.
Democratizing Access to Advanced Cyber Defense
One of the most transformative aspects of Foundation-sec-8B is its open-source licensing under Apache 2.0. In contrast to proprietary models confined within enterprise silos, this licensing model enables researchers, startups, educational institutions, and under-resourced security teams to integrate cutting-edge AI into their threat detection and response operations without incurring prohibitive costs. By making the model’s weights, tokenizer, and documentation publicly accessible, Cisco is effectively leveling the playing field in cybersecurity defense.
Small to mid-sized organizations, which often lack the infrastructure and budget to deploy or train large language models from scratch, now have access to a powerful tool that can be deployed on commercially available hardware. This accessibility supports greater inclusivity and diversity in cybersecurity, empowering entities in emerging markets and critical infrastructure sectors to build customized threat detection tools, train analysts, and accelerate response protocols.
Moreover, by reducing reliance on expensive, closed-source platforms, Foundation-sec-8B allows organizations to maintain greater sovereignty over their data and inference workflows. In highly regulated industries—such as healthcare, finance, and defense—this control is indispensable for ensuring compliance with data privacy standards and operational integrity.
Cultivating a Culture of Collaborative Defense
Cisco’s open-source release signals a shift in mindset from competition to collaboration. In an industry where information sharing has traditionally been fragmented and siloed, the model invites a more unified approach to cyber defense. Security practitioners are encouraged to contribute to the ongoing development of Foundation-sec-8B by refining use cases, submitting evaluation feedback, and building adjacent tools that extend the model’s functionality.
Platforms such as Hugging Face facilitate this collaboration, offering version control, community discussions, and model evaluation leaderboards. This fosters a virtuous cycle in which the community identifies weaknesses, proposes improvements, and co-develops security enhancements with the potential to benefit thousands of organizations globally.
Furthermore, open-source development reduces the risk of vendor lock-in, promoting interoperability between different security tools and platforms. The emergence of community-driven LLMs like Foundation-sec-8B encourages the development of plug-and-play architectures where AI modules can be embedded across endpoint detection systems, firewalls, SIEM solutions, and even hardware-based intrusion detection systems (IDS).
Addressing Trust, Security, and Model Robustness
While the benefits of open-source AI are considerable, they must be accompanied by strong safeguards to ensure security, accuracy, and trustworthiness. Cisco has anticipated these concerns by incorporating adversarial training techniques, rigorous benchmarking, and explainability features in Foundation-sec-8B. However, as the model gains broader adoption, continuous community vigilance will be crucial to mitigate potential misuse or unintended behavior.
A key concern is the possibility of malicious prompt injection or the generation of misleading security recommendations. To combat this, Cisco has made the model architecture transparent and modular, allowing third-party developers to embed custom guardrails, red-teaming protocols, and access control policies. By decentralizing the development process, the community can proactively harden the model against new attack vectors and data poisoning attempts.
Additionally, the model serves as a reference point for responsible AI development. Its documentation includes usage guidelines, ethical considerations, and operational best practices to ensure that AI tools are deployed with a clear understanding of their limitations and ethical implications. These measures are particularly relevant in critical applications such as national defense or infrastructure protection, where model errors could have far-reaching consequences.
Catalyzing Innovation in Security Tooling
Foundation-sec-8B is not simply a standalone tool—it is a foundation upon which future security innovations can be built. By offering a specialized knowledge base and flexible architecture, the model encourages the development of novel applications in AI-assisted forensics, malware classification, threat actor attribution, and automated security policy generation. The model’s training pipeline can be adapted to niche domains such as industrial control systems (ICS), Internet of Things (IoT) security, and secure software supply chains.
We are already witnessing early adopters integrating Foundation-sec-8B into Security Operations Centers (SOCs) as virtual analysts capable of processing alerts, triaging incidents, and synthesizing contextual insights. In academia, the model serves as a rich pedagogical tool for cybersecurity education, enabling students to explore AI’s role in digital defense without the constraints of proprietary software.
The ripple effect of this open release could spur the development of industry-wide frameworks for standardizing cybersecurity AI benchmarks, improving interoperability among AI models, and enhancing the explainability of security-related outputs. Long-term, this could contribute to the establishment of AI-driven defense consortiums and cross-sector threat intelligence alliances.
To contextualize Foundation-sec-8B’s potential impact, the following chart illustrates the increasing adoption of AI models in cybersecurity across industries from 2015 to 2025. The trend highlights a shift from experimental pilots to mainstream operationalization, with open-source models accelerating broader uptake.
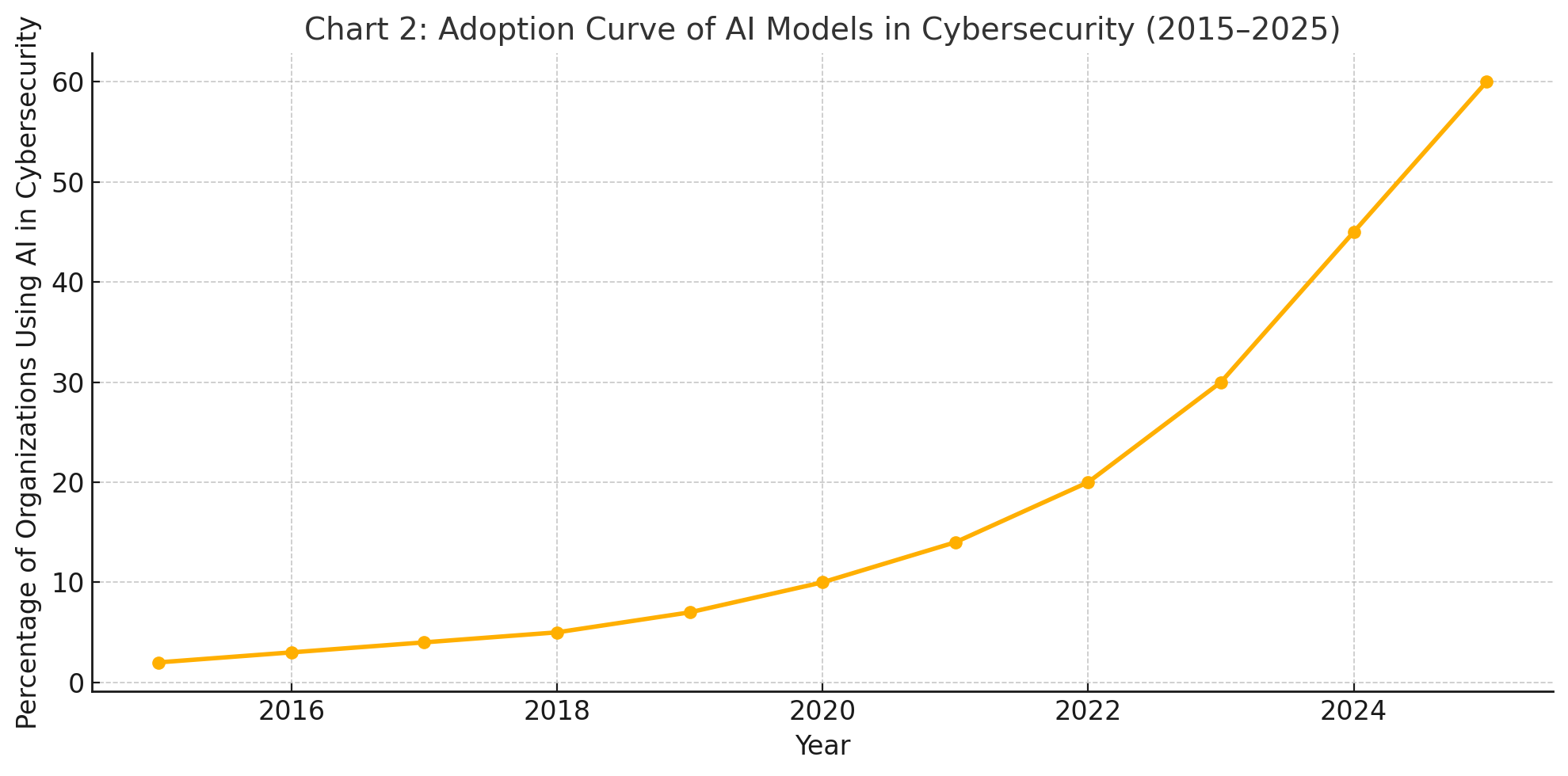
The surge in adoption post-2023 correlates with the release of more accessible models, improved hardware availability, and the formalization of regulatory guidelines around AI usage in security. Foundation-sec-8B, by virtue of its design and licensing, is positioned to amplify this trend further.
Paving the Way for Collaborative Cyber Defense
As cyber threats grow more intricate and adversaries leverage increasingly advanced tactics, the necessity for intelligent, responsive, and scalable defense mechanisms becomes paramount. Cisco’s launch of Foundation-sec-8B represents not just a technological achievement but a strategic inflection point in the evolution of cybersecurity. By releasing a high-performance, domain-specific AI model into the open-source ecosystem, Cisco is setting a new standard for how the cybersecurity community can collectively build and deploy effective defenses in an era defined by digital complexity.
The Foundation-sec-8B model addresses a long-standing gap in the cybersecurity toolset—namely, the lack of specialized AI models designed explicitly for security use cases. Unlike general-purpose language models, Foundation-sec-8B was conceived from the outset to operate within the linguistic, procedural, and tactical domains that define modern cybersecurity. It is finely attuned to understanding the nuances of threat intelligence, vulnerability data, incident response, and adversarial behaviors. The model’s robust performance in benchmark evaluations demonstrates the value of such specialization and affirms the benefits of training on targeted, domain-relevant corpora.
Equally significant is Cisco’s decision to embrace open-source licensing and public accessibility. In doing so, the company has taken a bold step toward dismantling traditional barriers to AI adoption in cybersecurity. Organizations that previously lacked the resources to engage with advanced AI technologies can now integrate Foundation-sec-8B into their security workflows without the constraints of vendor lock-in or proprietary limitations. This democratization of access is vital for ensuring that security capabilities are distributed equitably, not reserved solely for well-funded enterprises or government agencies.
Furthermore, Cisco’s approach encourages a culture of collaboration that is often absent in cybersecurity. By inviting researchers, developers, and practitioners to engage with and improve upon Foundation-sec-8B, the company is cultivating an ecosystem where collective intelligence and shared responsibility can flourish. This model of co-development aligns with the principles of responsible AI, fostering transparency, auditability, and community-driven improvements. As the cybersecurity threat landscape becomes more distributed and unpredictable, so too must the defense mechanisms become more cooperative and adaptive.
In operational terms, Foundation-sec-8B offers tangible benefits across a wide spectrum of cybersecurity applications. From accelerating incident triage in Security Operations Centers to enhancing vulnerability assessments and supporting automated threat intelligence generation, the model introduces efficiencies that were previously unattainable. It also facilitates the development of intelligent assistants and security co-pilots, paving the way for human-AI collaboration that augments—not replaces—human expertise.
Perhaps most importantly, Foundation-sec-8B serves as a blueprint for future development in AI-assisted cybersecurity. Its modular architecture, transparent design, and support for community contributions establish a precedent that other technology providers may follow. As threats evolve, so too must the tools that defend against them. The future will likely see a proliferation of similarly specialized models tailored to different aspects of cybersecurity, such as cloud-native threats, industrial control systems, and quantum-resilient cryptography. Cisco’s pioneering work with Foundation-sec-8B has laid the groundwork for this future.
In conclusion, the launch of Foundation-sec-8B marks a milestone not only for Cisco but for the cybersecurity community at large. It embodies a commitment to innovation, inclusivity, and collaboration that is sorely needed in today’s digital landscape. By aligning technological advancement with open access and community engagement, Cisco has demonstrated that meaningful progress in cybersecurity does not require secrecy or exclusivity—it requires shared purpose and collective action. As organizations around the world begin to integrate Foundation-sec-8B into their defense arsenals, they are not merely adopting a tool; they are participating in a broader movement toward smarter, safer, and more collaborative cyber defense.
References
- Cisco Foundation Models for Security — Official Announcement
https://blogs.cisco.com/security/introducing-cisco-foundation-models-for-security - Hugging Face Model Card for Foundation-sec-8B
https://huggingface.co/CiscoAI/Foundation-sec-8B - MITRE ATT&CK Framework
https://attack.mitre.org/ - OWASP Top 10 Security Risks
https://owasp.org/www-project-top-ten/ - NIST Cybersecurity Framework (CSF)
https://www.nist.gov/cyberframework - OpenAI on the Role of AI in Cyber Defense
https://openai.com/blog/ai-and-cybersecurity - Robust Intelligence (Cisco-acquired AI Security Firm)
https://www.robustintelligence.com/ - Llama 3.1 Architecture Overview – Meta AI
https://ai.meta.com/blog/meta-llama-3-open-foundation-models/ - Gartner: Why AI Is the Future of Cybersecurity
https://www.gartner.com/en/articles/why-artificial-intelligence-is-the-future-of-cybersecurity - SANS Institute: Integrating AI into SOC Operations
https://www.sans.org/white-papers/integrating-ai-into-soc-operations/
